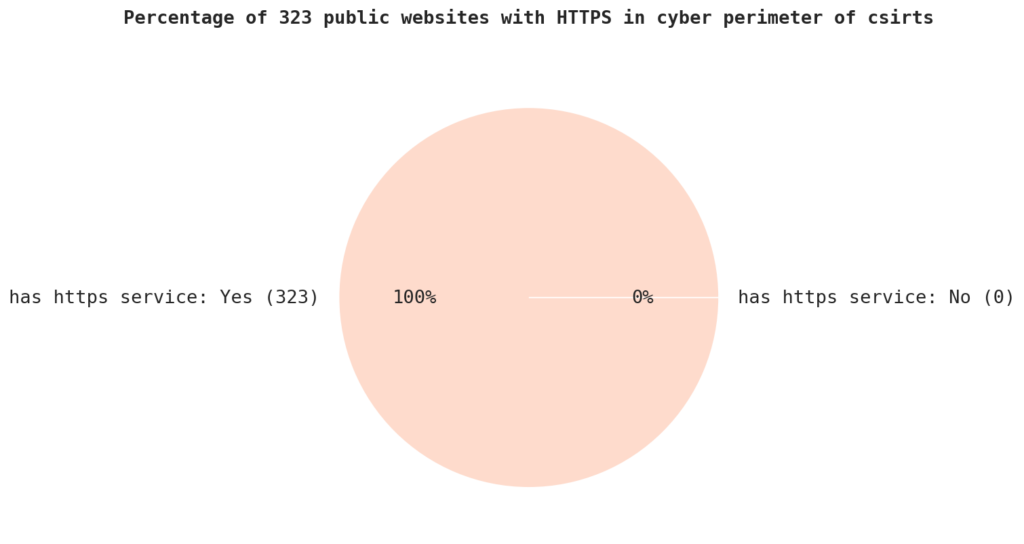
The cybersecurity report was generated analysing the cyber perimeter of public websites of 323 CERTs and CSIRTS in Europe and abroad. Those websites have been analysed for OWASP vulnerabilities, technologies used, HTTPS certificates, CVEs identified and IP information. The data showed that every single entity in the sample had an HTTPS service, a secure system for data transfer on the web.
SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are encryption methods used by HTTPS to protect confidential details, like login sign-ins and financial information.
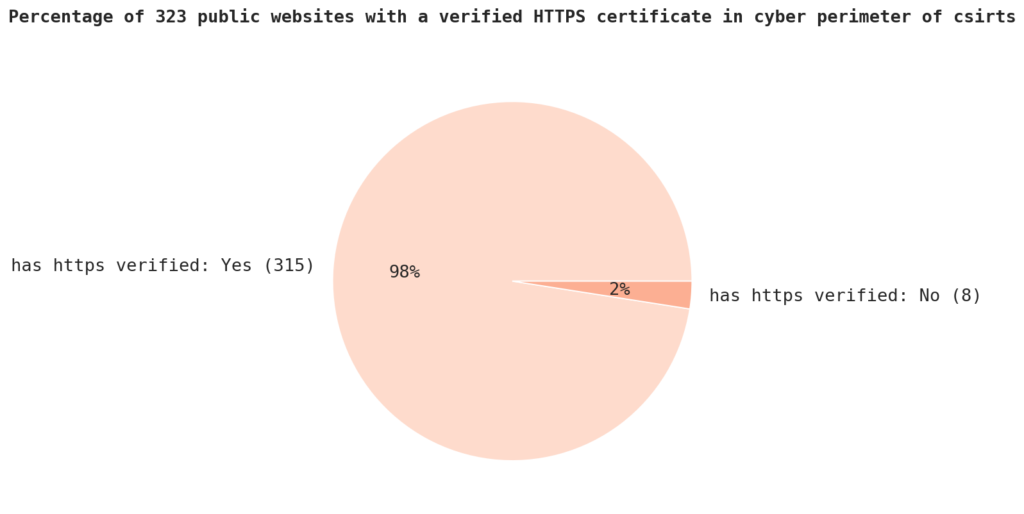
Of the sample, 97.5% has HTTPS verified, meaning that the certificate issued by the certificate authority (CA) has been verified as authentic and issued to the domain owner. This is an important security measure as it ensures that the website is not being impersonated by a third party.
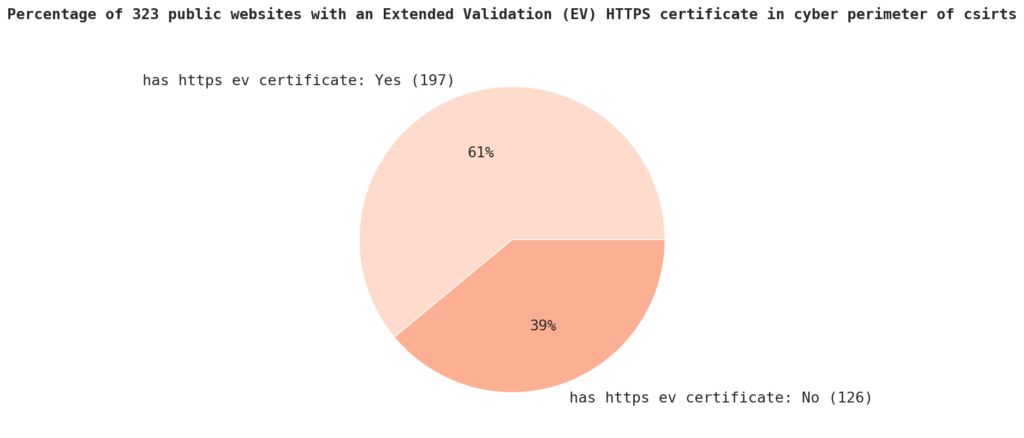
When it comes to HTTPS Extended Validation (EV) certificates, only 60.9% of the sample has one. An EV certificate is a type of HTTPS certificate that requires additional verification of the website’s identity by the issuing CA. This provides an extra layer of security for users as it ensures that the website is legitimate and not a phishing attempt.
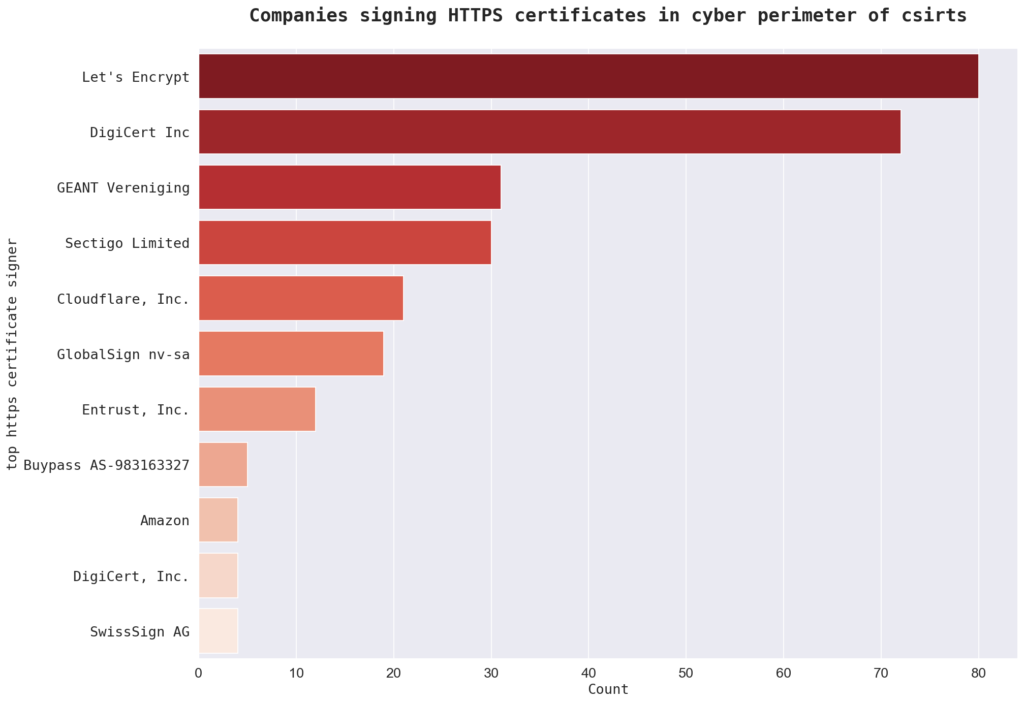
The top HTTPS certificate signer for the sample is “Let’s Encrypt” with 80 certificates, followed by “DigiCert Inc” with 72 certificates. The remaining top signers include “GEANT Vereniging,” “Sectigo Limited,” and “Cloudflare, Inc.” It is worth noting that there are 36 total certificate signers in the sample, indicating a diverse range of CAs being used.
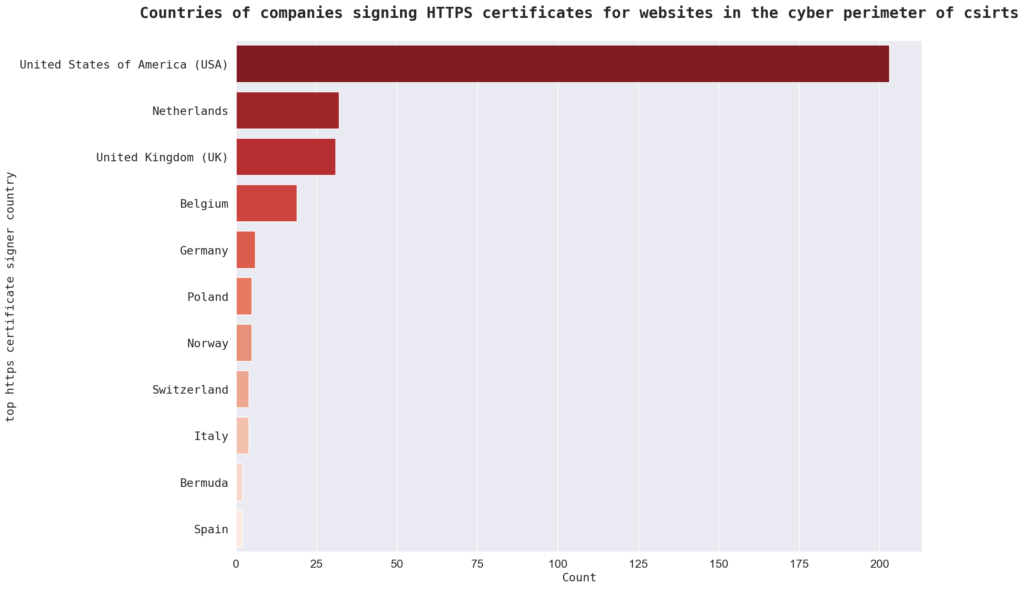
In terms of certificate signer countries, the top country is the United States with 203 certificates, followed by the Netherlands with 32 certificates. The remaining top countries include “China,” “United Kingdom,” and “Switzerland.” This suggests that the sample is geographically diverse and not limited to a particular region.
Overall, the data suggests that the sample places a high value on security and has implemented HTTPS to protect the transmission of sensitive information.
The report generated data which showed that every single entity in the sample had an HTTPS service, a secure system for data transfer on the web. SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are encryption methods used by HTTPS to protect confidential details, like login sign-ins and financial information.
Overall, the data suggests that the sample places a high value on security and has implemented HTTPS to protect the transmission of sensitive information.
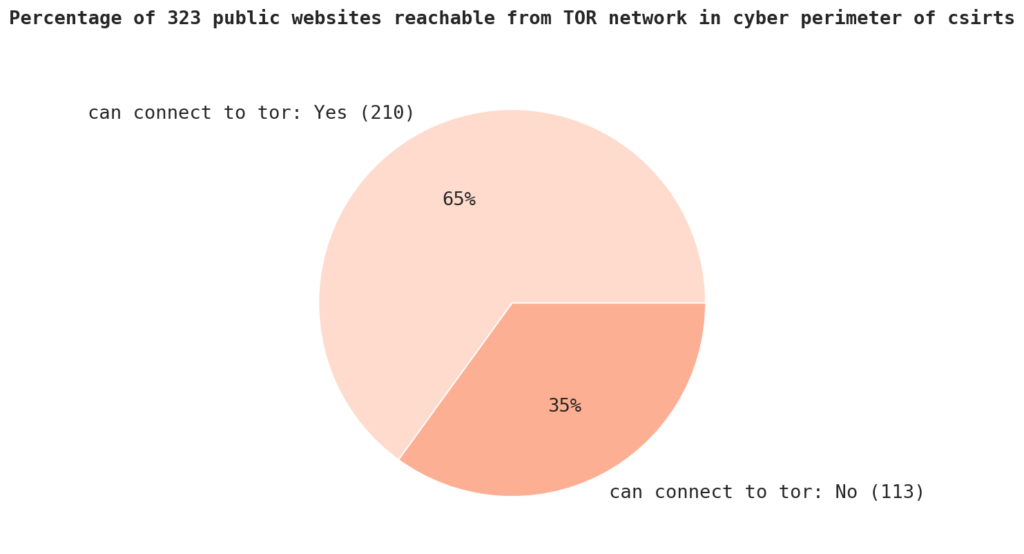
65% of the websites accepts connections from the TOR network, meaning that the attack surface, for example for DDOS attacks, could be reduced if anonymous connections from TOR network are denied by default. The majority of the sample has HTTPS verified and a significant portion has HTTPS EV certificates. The certificate signers and signer countries also indicate a diverse range of CAs and locations.
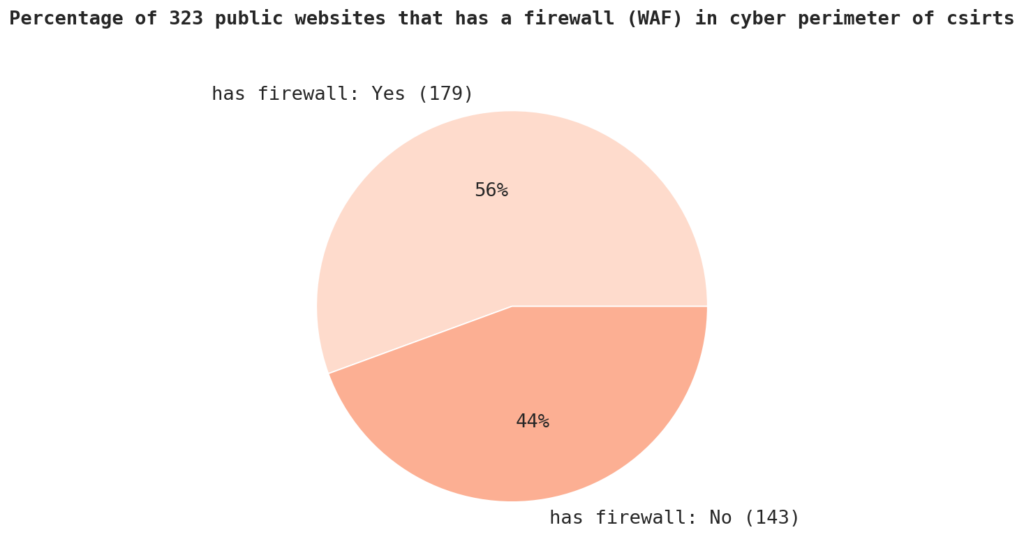
About 55.6% of the websites analysed has a WAF or web application firewall, with 179 websites of Certs and CSIRTS analysed have firewalls being present. A firewall is a security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. It is a critical component of an organization’s security infrastructure, as it can protect against cyber threats such as malware and hacking attempts.
The data provided in the report indicates that the sample has a variety of firewall types in use. 44% don’t have a firewall or no firewall was identified, with 143 instances. Other firewall types in the sample include “Cloudflare,” “BIG-IP AppSec Manager,” and “Kona SiteDefender.” There are a total of 19 firewall types in the sample.
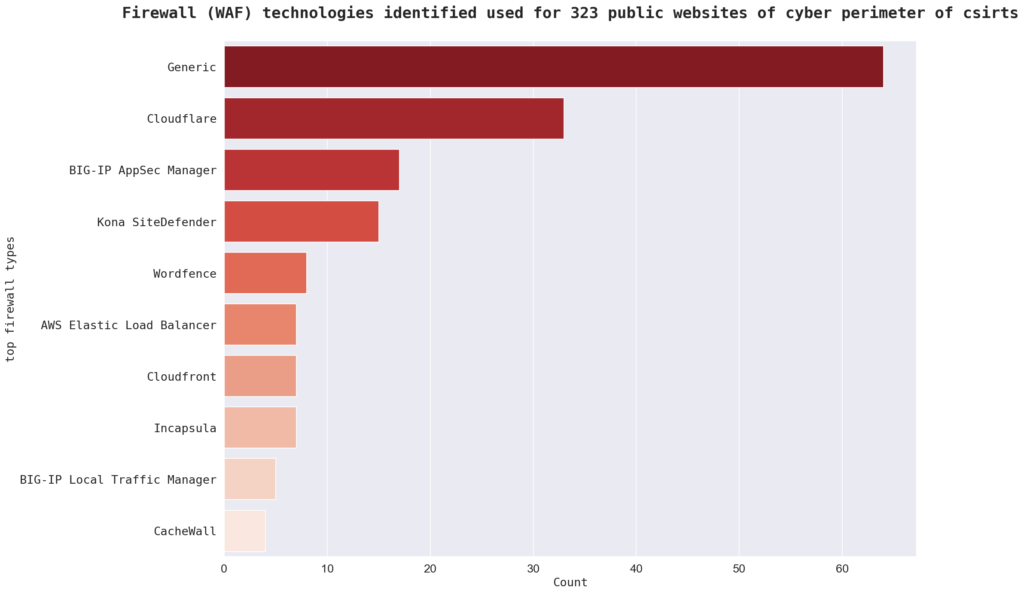
In terms of firewall manufacturers, the most common identified WAF creator is “Cloudflare Inc.”.
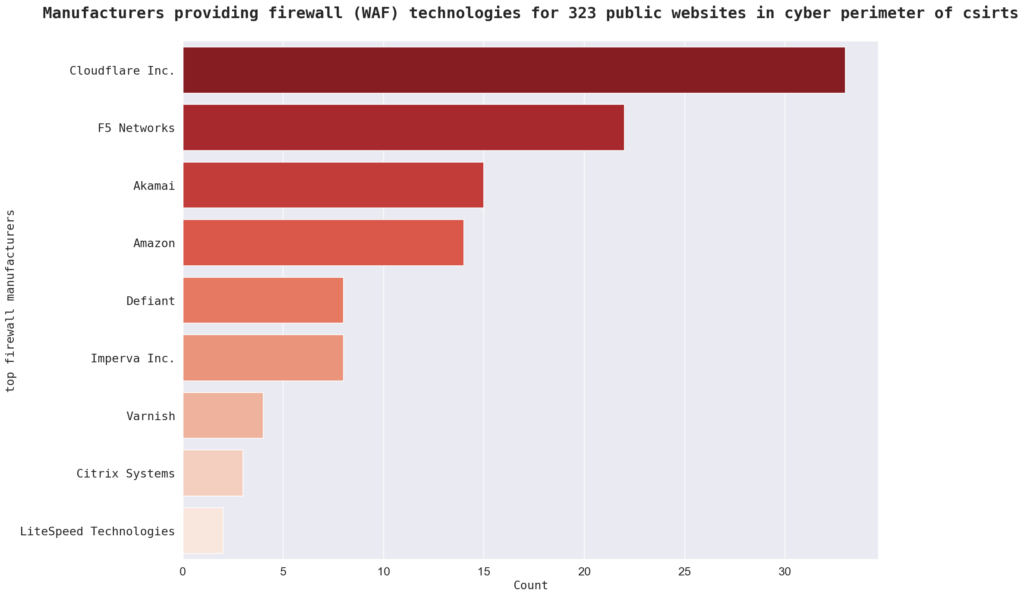
Other firewall manufacturers in the sample include “F5 Networks,” “Akamai,” and “Amazon.” There are a total of 16 firewall manufacturers represented in the sample.
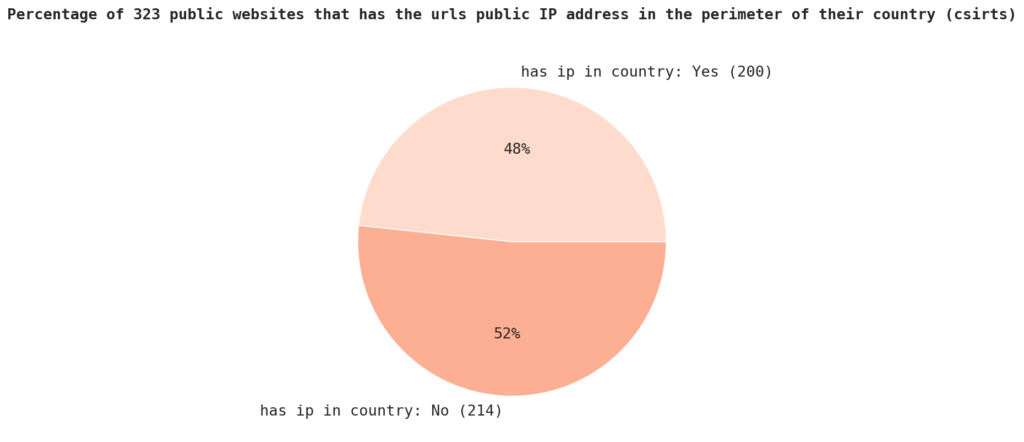
In terms of IP locations, only 48.3% of the sample has an IP located in the same country as the organization.
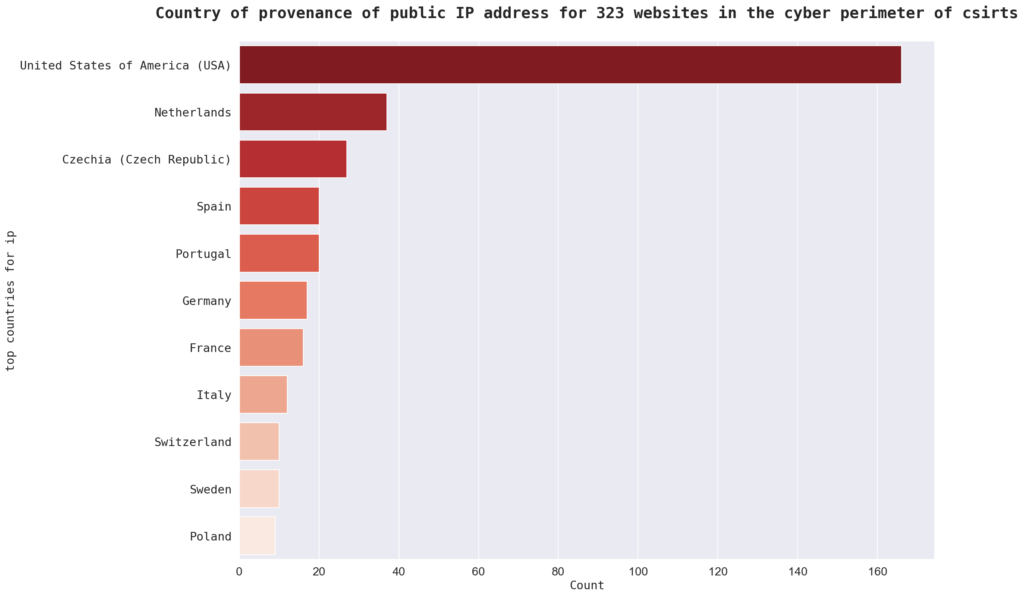
The top country for IP locations is the United States with 166 instances, followed by the Netherlands with 37 instances. Other top countries for IP locations in the sample include “Czechia (Czech Republic),” “Spain,” and “Portugal.” There are a total of 38 countries represented in the sample.
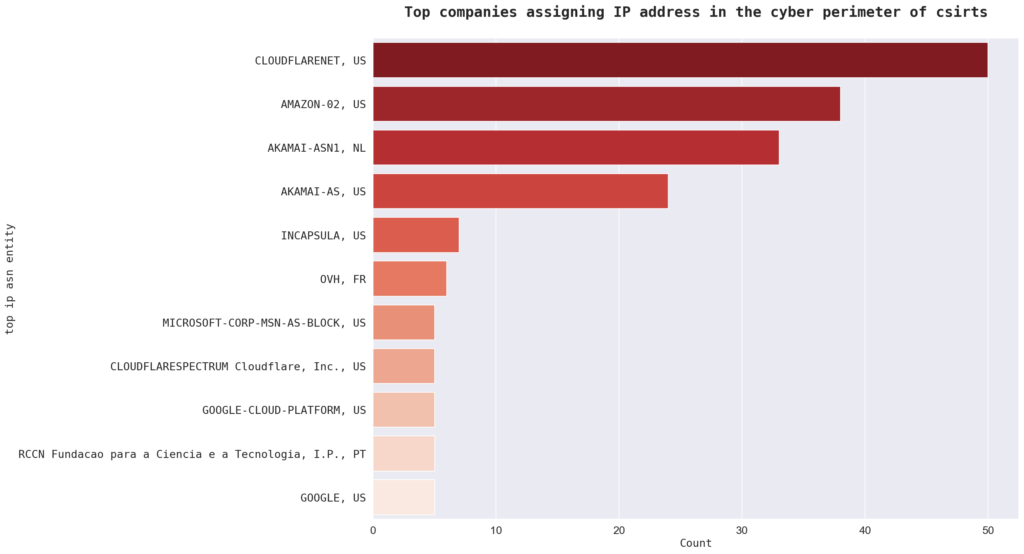
The top IP Autonomous System Number (ASN) entity in the sample is “CLOUDFLARENET, US” with 50 sites getting their IP address from Cloudflare, followed by “AMAZON-02, US” with 38 instances. An ASN is a unique identifier assigned to a network or group of networks that allows for the exchange of internet traffic between them. Other top ASN entities in the sample include “AKAMAI-ASN1, NL” and “AKAMAI-AS, US.” There are a total of 200 ASN entities represented in the sites analysed.
Overall, the data suggests that the sample has a diverse range of firewall types and manufacturers, with a relatively high percentage of organizations having a firewall in place. However, there is a significant portion of the sample with IP locations that are not in the same country as the organization, and a diverse range of ASN entities are present. It is important for organizations to carefully consider their firewall and IP configurations in order to ensure proper security measures are in place.
There are a total of 3,898 Common Vulnerabilities and Exposures (CVEs) present in the sites analysed. The average number of CVEs per site is 2.
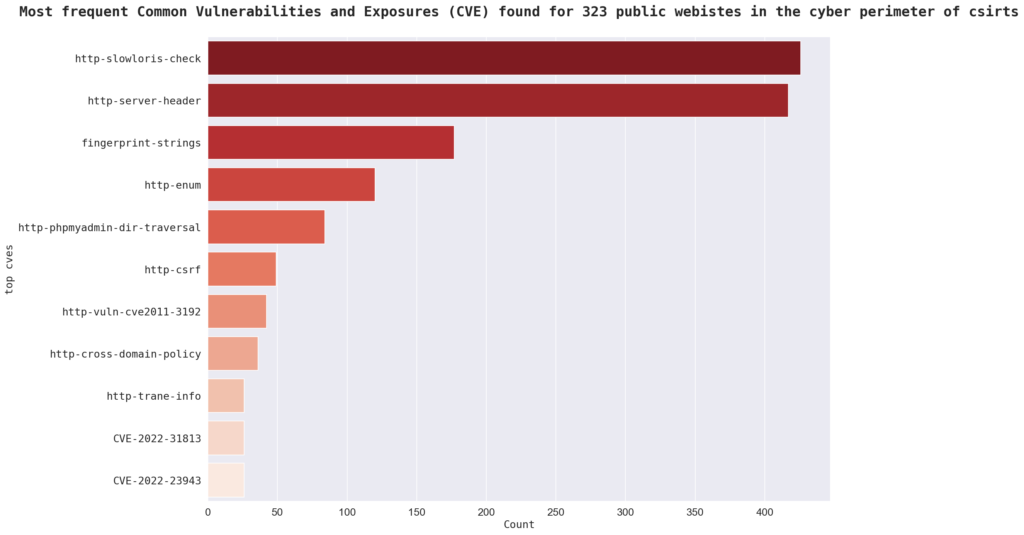
The top CVEs in the sample are “http-slowloris-check” with 426 instances, “http-server-header” with 417 instances, and “fingerprint-strings” with 177 instances. Other top CVEs in the sample include “http-enum,” “http-phpmyadmin-dir-traversal,” and “http-csrf.” There are a total of 1,000 CVEs in the sample.
A definition of the above 6 is provided as per NMAP documentation:
| Vulnerability | NMAP’s description |
| http-slowloris-check | Slowloris tries to keep many connections to the target web server open and hold them open as long as possible. It accomplishes this by opening connections to the target web server and sending a partial request. By doing so it starves the http server’s resources causing Denial Of Service. |
| http-server-header | Uses the HTTP Server header for missing version info. |
| fingerprint-strings | Prints the readable strings from service fingerprints of unknown services. |
| http-enum | Enumerates directories used by popular web applications and servers. |
| http-phpmyadmin-dir-traversal | PHP file inclusion vulnerability allows remote attackers to include local files via the $__redirect parameter possibly involving the subform array |
| http-csrf | This script detects Cross Site Request Forgeries (CSRF) vulnerabilities. It will try to detect them by checking each form if it contains an unpredictable token for each user. Without one an attacker may forge malicious requests. To recognize a token in a form, the script will iterate through the form’s attributes and will search for common patterns in their names. If that fails, it will also calculate the entropy of each attribute’s value. A big entropy means a possible token. |
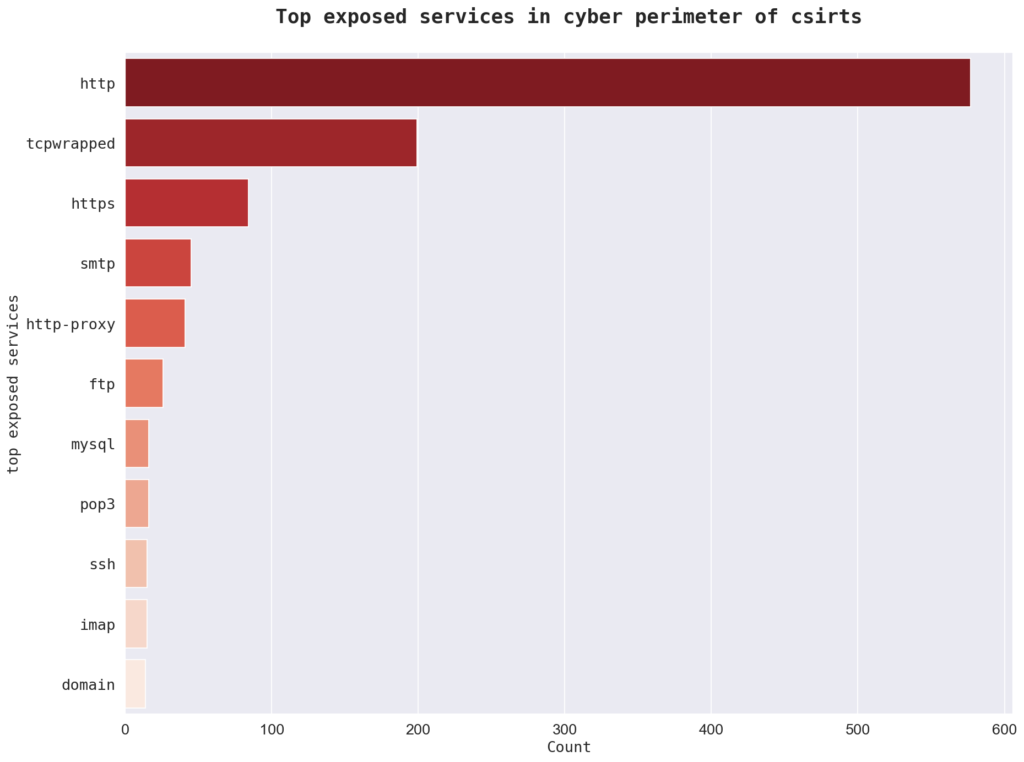
The top used services in the sample are “80 http” with 280 instances, “443 http” with 216 instances, and “443 https” with 84 instances. Other top used services include “8080 http,” “8443 http,” and “80 http-proxy.” There are a total of 192 services in the analysed sites.
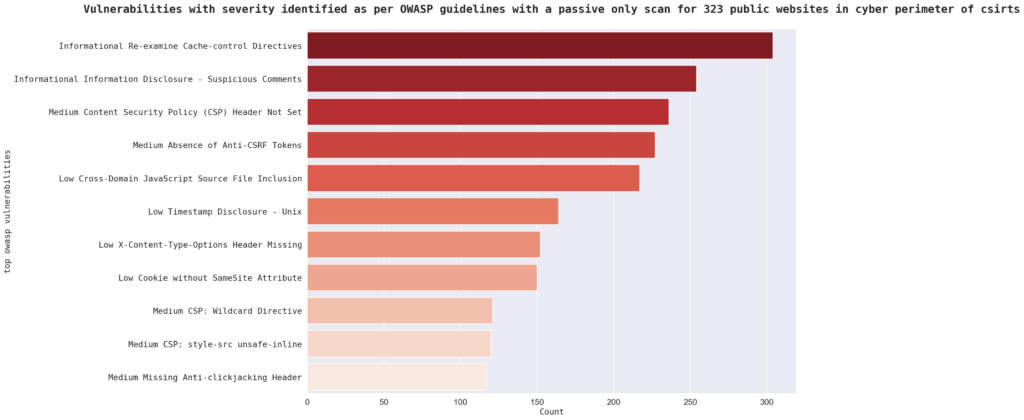
In terms of Open Web Application Security Project (OWASP) vulnerabilities, the most common is “Informational: Re-examine Cache-control Directives” with 304 instances. This is followed by “Informational: Information Disclosure – Suspicious Comments” with 254 instances and “Medium: Content Security Policy (CSP) Header Not Set” with 236 instances. Other top OWASP vulnerabilities in the sample include “Medium: Absence of Anti-CSRF Tokens” and “Low: Cross-Domain JavaScript Source File Inclusion.” There are approximately 3000 OWASP vulnerabilities identified in the cybersecurity research.
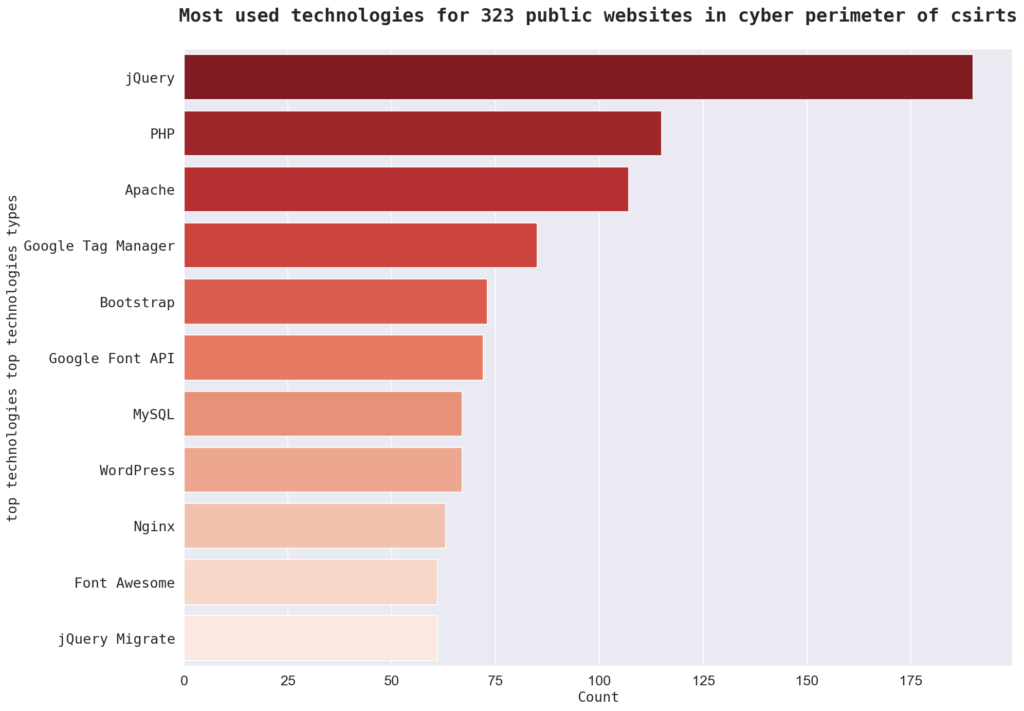
When it comes to technologies, the most common in the sample is “jQuery” with 190 instances, followed by “PHP” with 115 instances and “Apache” with 107 instances. Other top technologies in the sample include “Google Tag Manager,” “Bootstrap,” and “Google Font API.” There are a total of 156 technologies in the sample.
It is important for organizations to be aware of the potential vulnerabilities present in their systems and to take steps to mitigate the risks associated with them. This includes regularly updating software and monitoring for new or emerging vulnerabilities. It is also important to have a robust security infrastructure in place, including firewalls and secure protocols, to protect against potential threats.
In addition to vulnerabilities, it is important for organizations to consider the technologies and services they are using. Ensuring that these technologies and services are regularly updated and secure is essential in maintaining the overall security of the organization. It is also important to carefully evaluate the risks and benefits of any new technologies or services before implementing them.
The security score calculated for the CERT/CSIRTS sites in the perimeter was 232.9, more information here: Introducing an objective data based global cybersecurity score index
Overall, the data extracted from the 323 websites of CSIRTS analysed highlights the importance of continuously monitoring and addressing potential vulnerabilities and security risks. By taking proactive measures to protect against threats, organizations can better protect themselves and their sensitive data.
