The following is a list of various GitHub repositories that relate to the security of IoT devices and CCTV cameras. These tools can be used to search for and exploit vulnerabilities, analyze network traffic, and control your devices where you have permission on the device itself and the network it is connected to. To limit the risk of having potentially vulnerable devices, always update the home camera software and monitor the manufacturer’s homepage for cybersecurity updates.
The list of tools relating to video security and home camera penetration testing:
- BirDuster/dirbuster: This is a tool that can be used to search for and exploit vulnerabilities in various types of IoT devices. The tool can be used to perform a variety of tasks, such as identifying potential vulnerabilities, exploiting known vulnerabilities, and creating custom payloads. The repository is maintained by ytisf and is available at https://github.com/ytisf/BirDuster.
- CVE-2021-36260: This is a Common Vulnerabilities and Exposures (CVE) entry for a vulnerability in a specific Hikvision camera software. The vulnerability allows an attacker to gain unauthorized access to the camera’s web interface. The repository is maintained by Aiminsun and is available at https://github.com/Aiminsun/CVE-2021-36260.
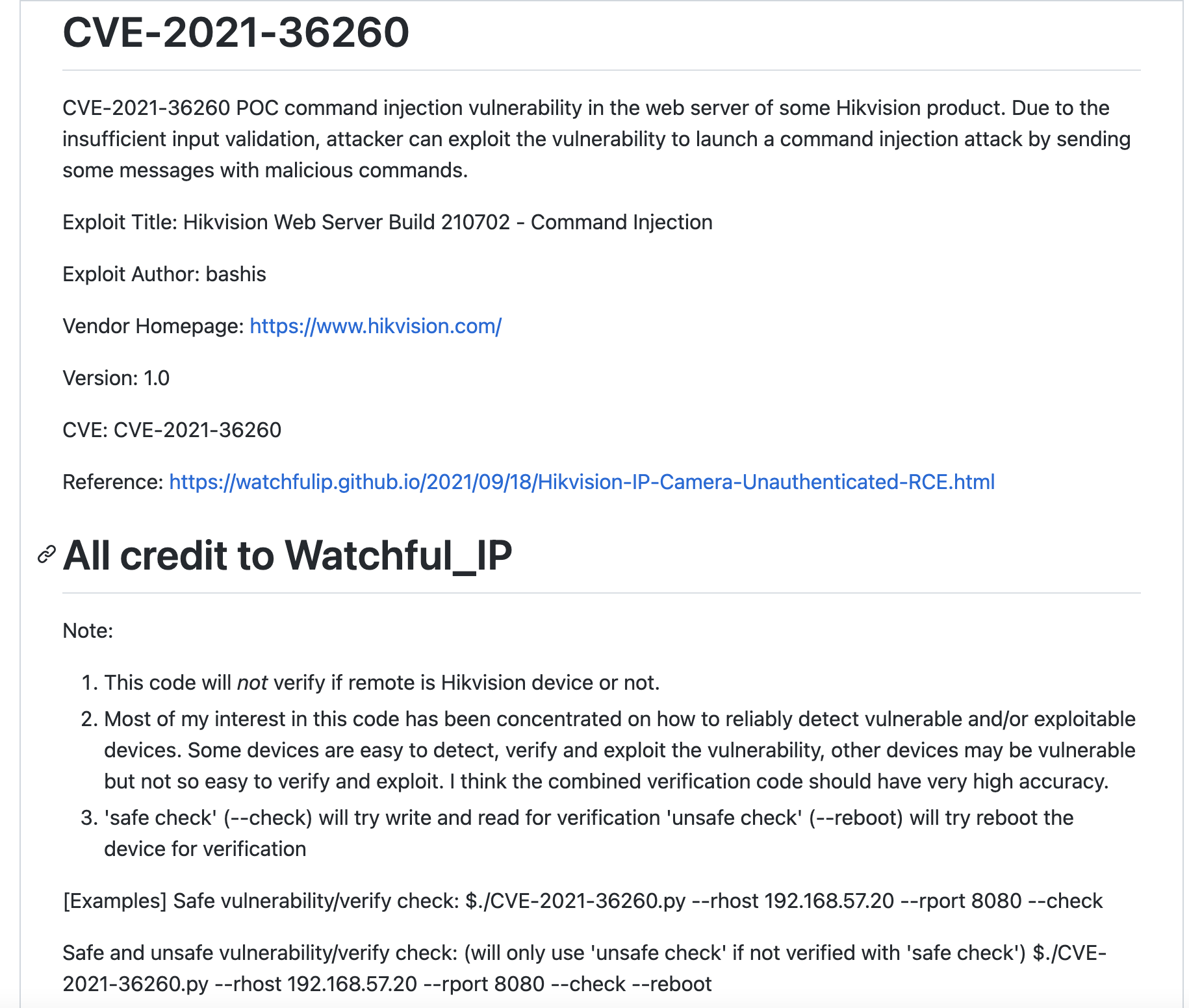
- Cam-Hackers: This is a tool that can be used to hack into and control CCTV cameras. The tool can be used to perform a variety of tasks, such as identifying potential vulnerabilities, exploiting known vulnerabilities, and creating custom payloads. The repository is maintained by Cam-Hackers and is available at https://github.com/AngelSecurityTeam/Cam-Hackers.
- Ezviz Camera CCTV Logging: This tool allows users to access and control CCTV cameras made by Ezviz. It can be utilized for various logging purposes and saving into a hard disk drive. The repository is maintained by JaviPalacio and can be accessed at https://github.com/JaviPalacio/EzvizCamera_CCTV_Logging
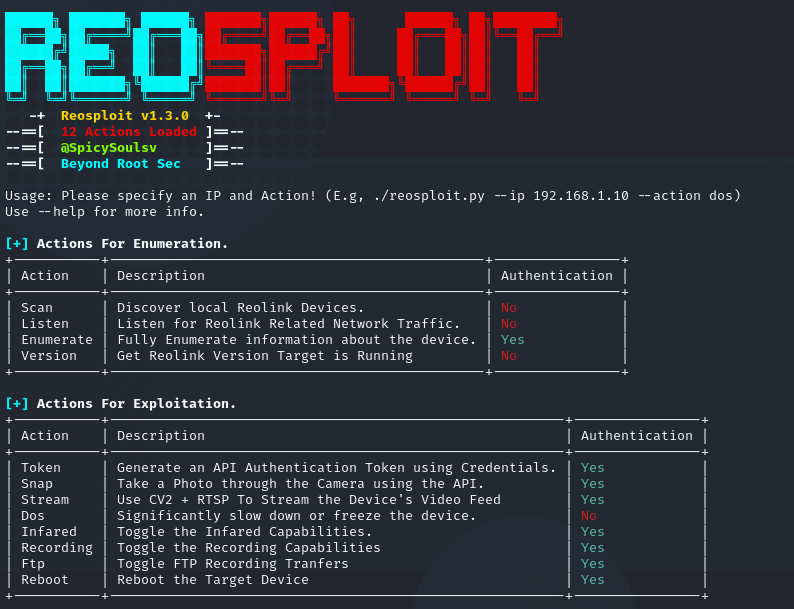
- Reosploit: This is a tool that can be used to scan for and exploit known vulnerabilities in Reolink CCTV cameras. The tool can be used to perform a variety of tasks, such as identifying potential vulnerabilities, exploiting known vulnerabilities, and saving snapshots from the camera.
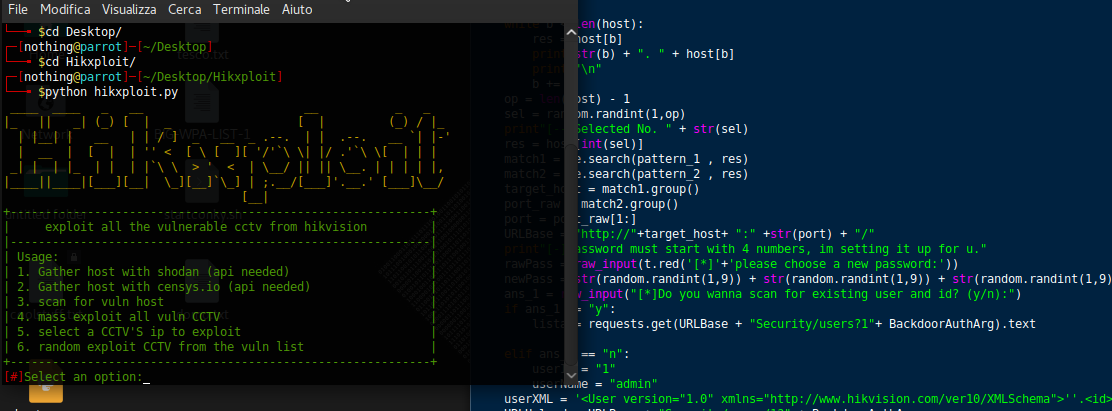
- Hikxploit: This is a tool that can be used to exploit known vulnerabilities in Hikvision CCTV cameras. The tool can be used to perform a variety of tasks, such as identifying potential vulnerabilities, exploiting known vulnerabilities, and creating custom payloads. The repository is maintained by M0tHs3C and is available at https://github.com/M0tHs3C/Hikxploit.
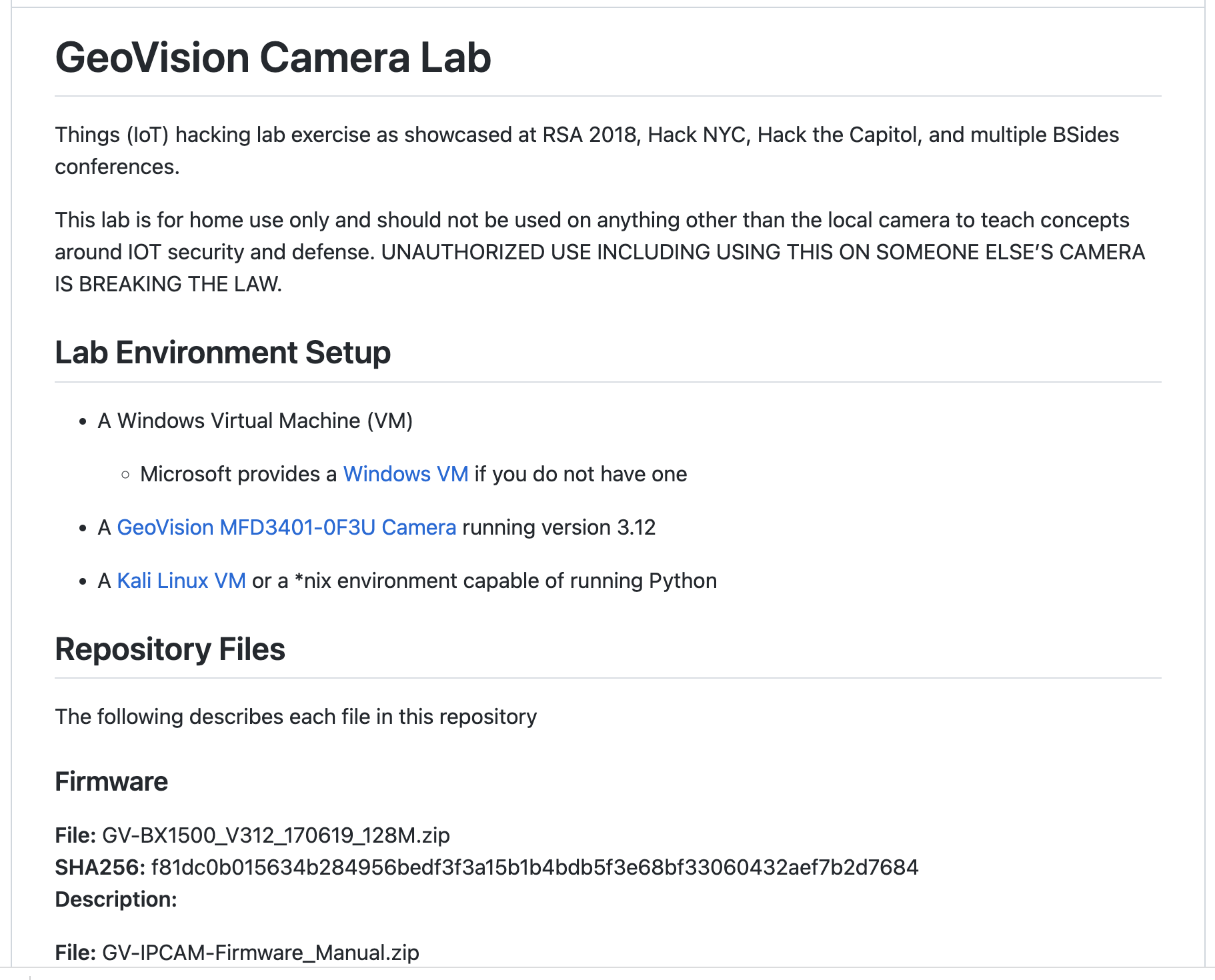
- IoTCameraLab: This is a tool that can be used to analyze the security of IoT cameras. The tool can be used to study vulnerabilities of Geovision Inc. IP Camera: Video/Access Control Multiple Remote Command Execution, Multiple Stack Overflows, Double free, Unauthorized Access. The repository is maintained by grimm-co and is available at https://github.com/grimm-co/IoTCameraLab.
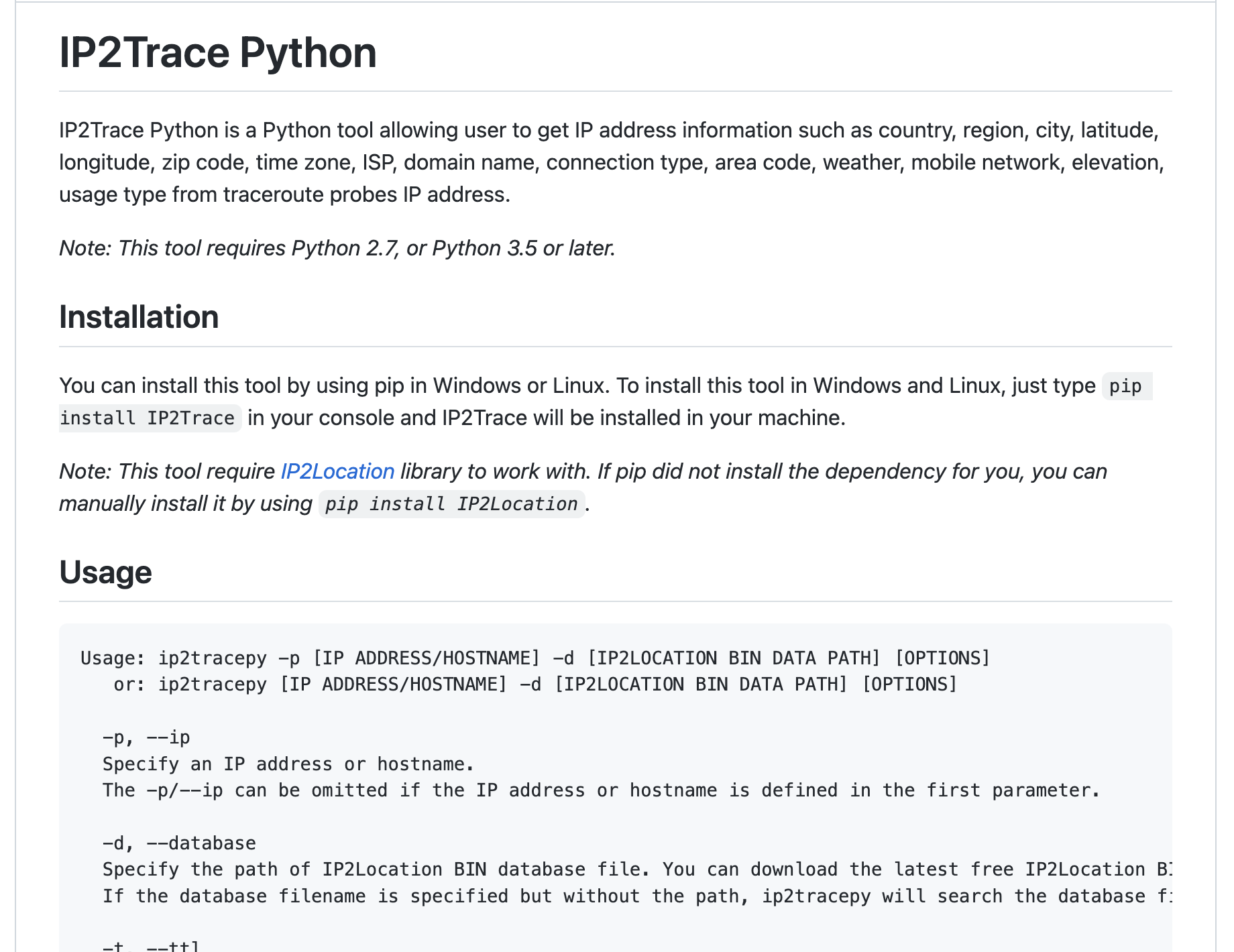
- ip2trace-python: This is a python tool that can be used to trace the geolocation of an IP address. The tool can be used to perform a variety of tasks, such as identifying potential vulnerabilities, exploiting known vulnerabilities, and creating custom payloads. The repository is maintained by ip2location and is available at https://github.com/ip2location/ip2trace-python
- PacketAnalyzer: This is a tool that can be used to analyze network traffic. The tool allows users to capture, view, and analyze network packets in real-time. It can be used to detect and troubleshoot network issues, identify potential security threats, and perform forensic analysis. The repository is maintained by rishabhjoshi and is available at https://github.com/rishabhjoshi/Network-Packet-Analyzer
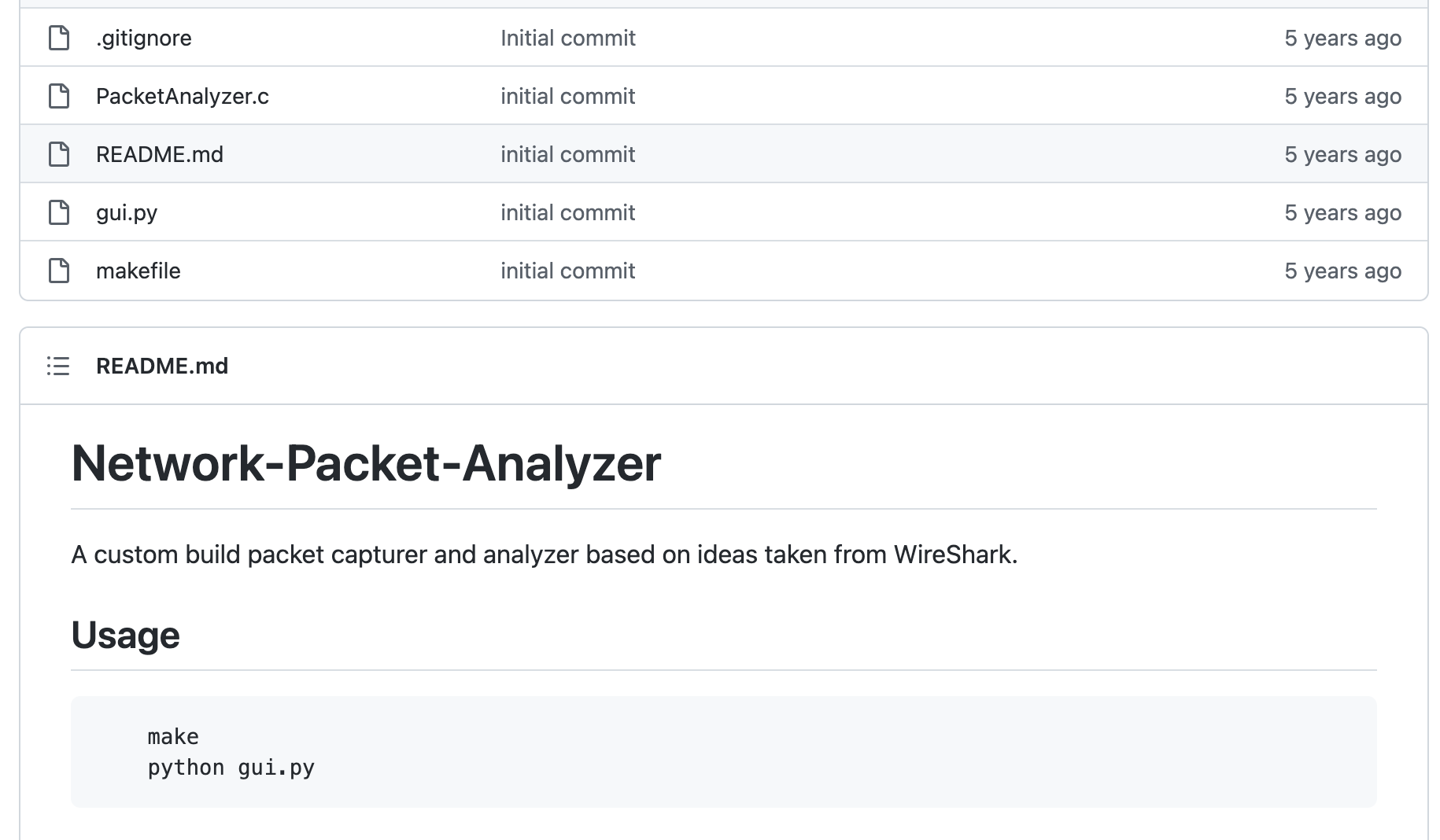
- SearchCAM: This is a tool that can be used to search for and access CCTV cameras. It uses Shodan search engine to identify and locate CCTV cameras connected to the internet. The tool can be used to perform reconnaissance, identify potential security vulnerabilities and perform penetration testing. The repository is maintained by AngelSecurityTeam and is available at https://github.com/AngelSecurityTeam/SearchCAM
- Vailyn: This is a tool that can be used to analyze the security of IoT devices. It can be used to perform vulnerability scanning and reconnaissance on IoT devices, identifying known vulnerabilities and potential attack vectors. The tool can also be used to perform penetration testing on IoT devices by exploiting known vulnerabilities. The repository is maintained by VainlyStrain and is available at https://github.com/VainlyStrain/Vailyn
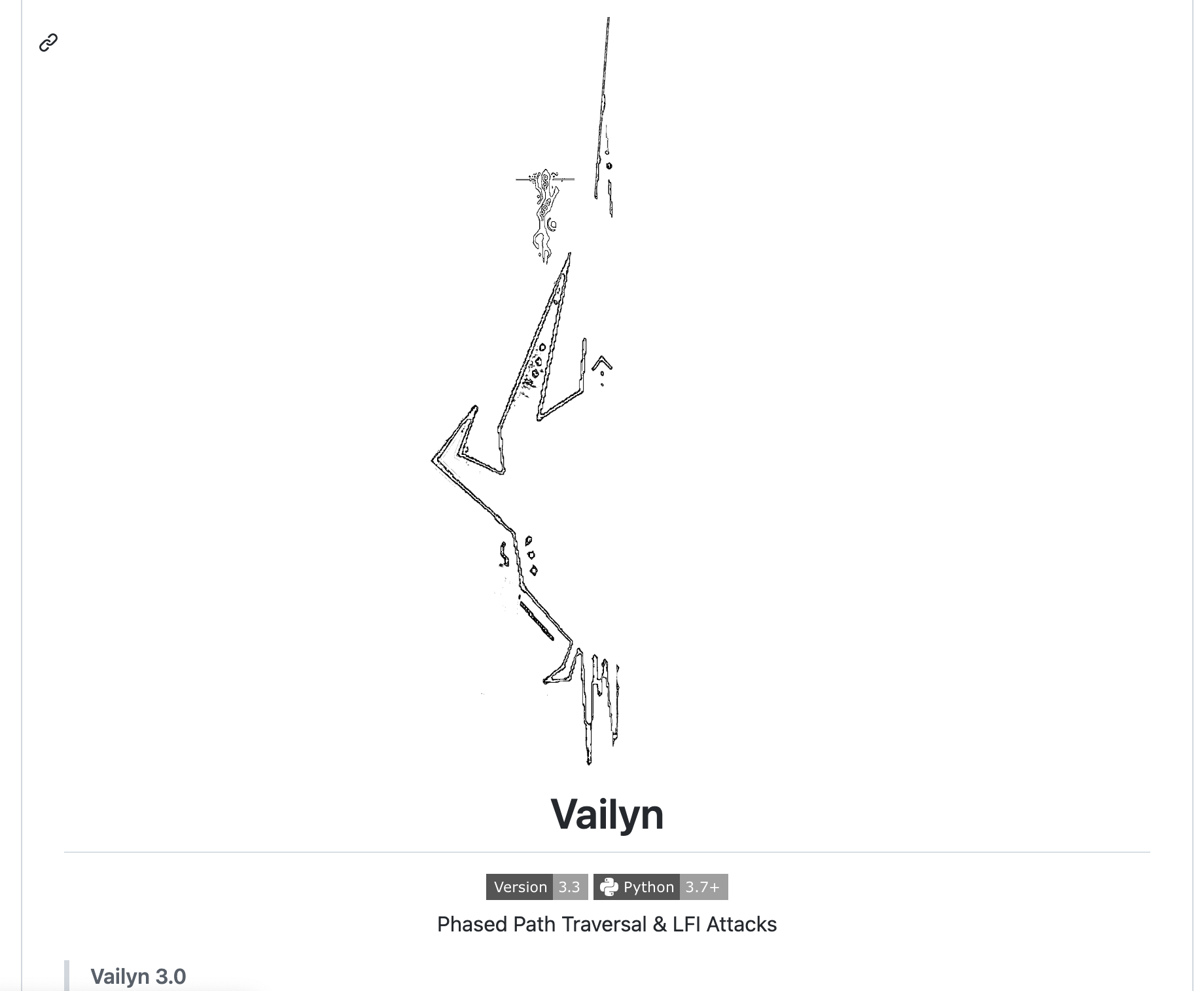
- shodan-dorks: This is a list of search queries that can be used with the Shodan search engine to find specific types of Internet-connected devices. These search queries are also known as “dorks” and can be used to identify devices with known vulnerabilities, open ports, and other security issues. The repository is maintained by humblelad and is available at https://github.com/humblelad/Shodan-Dorks
- NMAP: This is a world-renowned open-source software for network scanning. It can be used to perform reconnaissance, identify hosts and services on a computer network, and perform vulnerability scanning. NMAP is a versatile tool for network administrators and cybersecurity professionals. The repository is maintained by nmap and is available at https://github.com/nmap/nmap
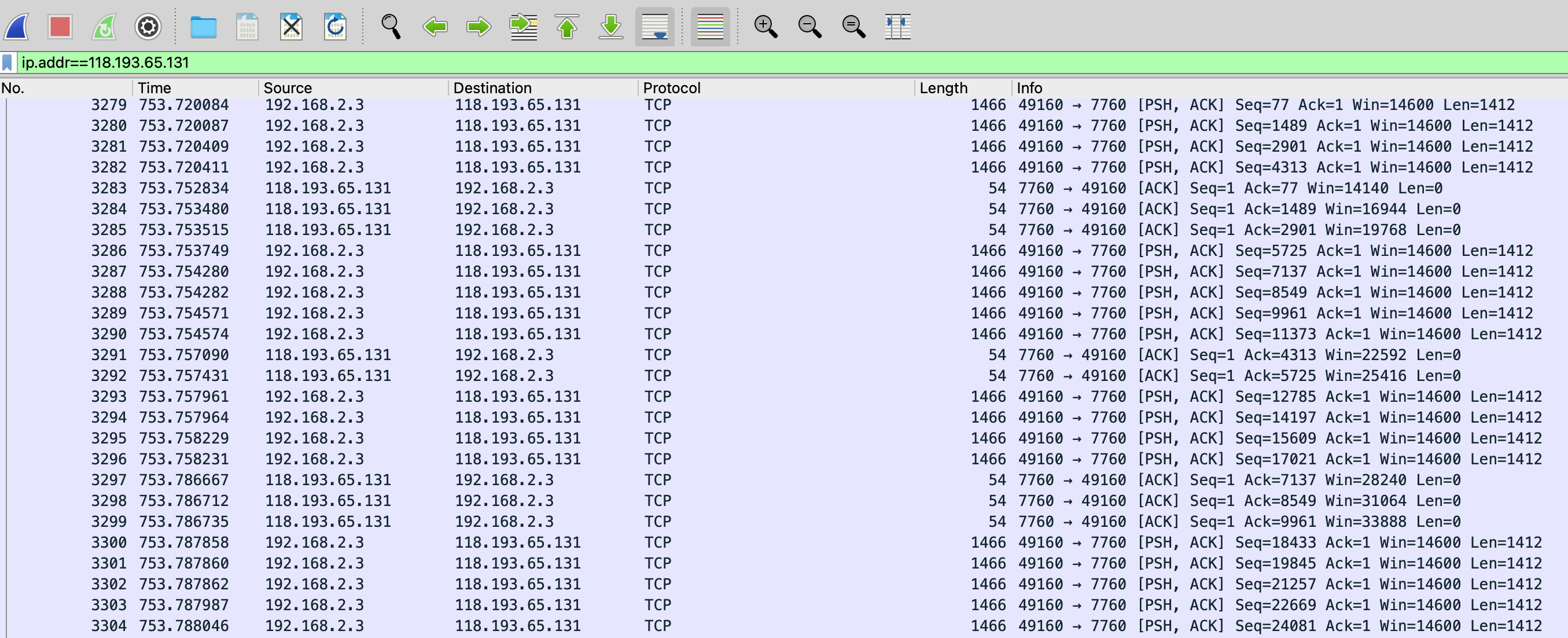
- Wireshark: This is a top-class software for network analysis and data and packet segmentation. It includes a user-friendly interface and can be used to capture, view and analyze network packets in real-time. Wireshark can be used to troubleshoot network issues, identify potential security threats, and perform forensic analysis. The repository is maintained by wireshark and is available at https://github.com/wireshark/wireshark
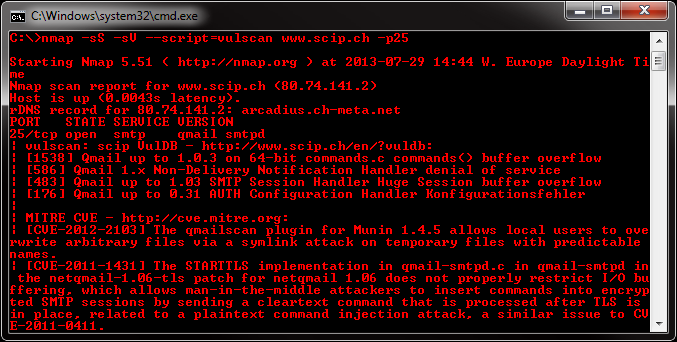
- vulscan: This is a Nmap script that can be used to check for the presence of known vulnerabilities on a target host. The script uses a database of known vulnerabilities and can be used to identify potential attack vectors, perform vulnerability scanning and penetration testing. The repository is maintained by scipag and is available at https://github.com/scipag/vulscan.git.
DISCLAIMER: All the information here is presented for educational purposes and to be used only with permission on devices and networks you own and control.
In summary, the above-mentioned repositories are a collection of tools and scripts that can be used to search for and exploit vulnerabilities in IoT devices and CCTV cameras. These tools can be used for reconnaissance, vulnerability scanning, penetration testing, and forensic analysis. They are a valuable resource for cybersecurity professionals and network administrators to enhance the security of their networks.
