The study analyzed approximately 3,000 websites in six countries (Turkey, Italy, India, Brazil, Argentina, and Indonesia) that make up the national cyber perimeters of those countries. These websites belonged to institutions, private companies, and organizations that provide essential services or are part of the supply chain in the respective countries. The study used a variety of tools, including open source tools like NMAP and custom Python code, as well as AWS cloud-based infrastructure, to gather and analyze data. The goal of the study was to define a security score for each country’s cyber perimeter based on a set of 18 key performance indicators (KPIs). These KPIs were weighted according to their relevance in determining the overall security score of a country, with some being given a higher weighting if they had a greater impact on the score. The results of the study were then aggregated to compare the national cyber security perimeters of the different countries. In this article 7 of the total KPIs defined to calculate a security score for a country and hence a global data based cybersecurity index. The 7 KPIs are specified in the following questions and measuring the data of the scans results.
| What percentage of websites in cyber perimeters has a firewall (WAF) ? |
| What are the most used firewall (WAF) technologies for websites in cyber perimeters? |
| What are the top firewall technologies manufacturers for websites in cyber perimeters? |
| What percentage of websites in cyber perimeters have their public IP in country? |
| What are the top IP ASN entities for websites in cyber perimeters? |
| What are the top countries where public IPs of websites in cyber perimeters are from? |
| What are the most used identified operating systems for websites in cyber perimeters? |
What percentage of websites in cyber perimeter has a firewall (WAF) ?
A web application firewall or WAF defends a website from common attack vectors and manipulation and is necessary in making a site more secure. Hence the greater number of sites protected by a firewall the more secure and less prone to falling from attacks is the cyber perimeter of a country.
The following results identify which percentages of the cyber perimeter of a country use a Web Application Firewall:
| Country | Percentage of sites in cyber perimeter use a firewall (WAF) |
| Brazil | 33% |
| Turkey | 69% |
| Indonesia | 36% |
| Argentina | 40% |
| India | 29% |
| Italy | 52% |
| Average | 42% |
What are the most used firewall (WAF) technologies for websites in cyber perimeters?
A web application firewall or WAF helps protecting a site from different types of attack and monitors also the connections being made to the site in order to reduce the attack surface and deny unrequested users from accessing the site.
| Country | Most used identified WAF technologies sorted by number of occurrences |
| Brazil | Generic BIG-IP AppSec Manager BIG-IP Local Traffic Manager |
| Turkey | Generic BIG-IP AppSec Manager NetScaler AppFirewall |
| Indonesia | Generic BIG-IP AppSec Manager Fortiweb |
| Argentina | Cloudflare Generic BIG-IP Local Traffic Manager |
| India | Generic Asp.net Microsoft BIG-IP AppSec Manager |
| Italy | Generic Cloudfront BIG-IP AppSec Manager |
What are the top firewall technologies manufacturers for websites in cyber perimeters?
A WAF or Web Application Firewall protect a website and increase its security and overall resilience, its important to know which companies are creating these WAFs because they are the ones with important information on the website, its structure and have a pivotal role in making sure the software they provide is secure and is not controlled by hostile agents. The results listed exclude the none and unknown types.
| Country | Top known WAF manufacturers companies |
| Brazil | F5 Networks Microsoft Amazon |
| Turkey | F5 Networks Citrix Systems Microsoft |
| Indonesia | F5 Networks Fortinet Cloudflare |
| Argentina | F5 Networks Cloudflare Fortinet |
| India | Microsoft F5 Networks Amazon |
| Italy | Amazon F5 Networks Varnish Software |
All WAF manufacturers above are companies from the United States with the exception of Varnish Software which is Norwegian.
What percentage of websites in cyber perimeters have their public IP in country?
The internet protocol address or IP is a set of 4 group of numbers that identify an internet connected device, specifically named IPv4. For each website taken into consideration and analysed in the cyber perimeter of a country, the corresponding public IPv4 address has been checked. Even though this address is just the public one and behind it there could be other address representing machines where the actual data of a website is stored, it can be taken as an example of how much of the software stack is kept in country. The following results highlight whether the public IP address of a website in the cyber perimeter of a country are actually from that country. A higher percentage means that – at least for the public address at the top of the tech stack – the IPs are from the same country as the websites in consideration which can be an example of control of that country of its cyber perimeter and hence of its resiliency.
| Country | Percentages of websites that have the public IP address in their country |
| Brazil | 78% |
| Turkey | 93% |
| Indonesia | 82% |
| Argentina | 76% |
| India | 85% |
| Italy | 69% |
| Average | 81% |
What are the top countries where public IPs of websites in cyber perimeter are from?
For a stronger and more resilient cyber perimeter, it would be beneficial if websites in the cyber perimeter of a country had their public IP address in that country, but if they don’t, which country is the IP address of the site from? The following results highlight the top 3 countries that IP address are from if not from the country taken into consideration.
| Country | Identified country of provenance of public IP address for websites in the cyber perimeter of a country, except the country itself |
| Brazil | United States of America (USA) Portugal Germany |
| Turkey | United States of America (USA) United Kingdom |
| Indonesia | United States of America (USA) Singapore Malaysia |
| Argentina | United States of America (USA) Canada Colombia |
| India | United States of America (USA) Germany Canada |
| Italy | United States of America (USA) France United Kingdom |
What are the top IP ASN entities for websites in cyber perimeter?
The internet protocol or IP address is assigned to a website by specific entities/companies which have ranges that they can use. IP ASN or internet protocol autonomous systems numbers are used by the internet network to route traffic to a website, these blocks are assigned by companies to sites in the cyber perimeter of a country. The following table highlights the top 3 ASN entities assigning those IP numbers per country by number of occurrences:
| Country | Top 3 IP ASN entities for websites in the cyber perimeter of a country |
| Brazil | V tal, BR MICROSOFT-CORP-MSN-AS-BLOCK, USA SERVICO FEDERAL DE PROCESSAMENTO DE DADOS – SERPRO, BR |
| Turkey | TTNET, TR ULAKNET, TR VEDOP-II, TR |
| Indonesia | TELKOMNET-AS-AP PT Telekomunikasi Indonesia, ID JARDIKNAS-AS-AP Pustekkom, ID DEPKEU-AS-ID Pusat Sistem Informasi dan Teknologi Keuangan Pusintek , ID |
| Argentina | CLOUDFLARENET, USA Telecom Argentina S.A., AR Agencia de Sistemas de Informacion, Gobierno de la Ciudad Autonoma de Buenos Aires, AR |
| India | NICNET-VSNL-BOARDER-AP National Informatics Centre, IN NKN-CORE-NW NKN Core Network, IN MPONLINELTD-AS-IN MPOnline Ltd, IN |
| Italy | ARUBA-ASN, IT AMAZON-02, USA FASTWEB, IT |
What are the most used identified operating systems for websites in cyber perimeters?
Each website in the cyber perimeter of a country taken into consideration has been analysed to try and understand its operating system, or the OS of the server hosting the website or present at the top of the stack, these were the results obtained for the OS that were identified, excluding load balancers.
| Country | Identified Operating Systems for websites in the cyber perimeter of country, without load balancers, in order of occurrences |
| Brazil | Linux 4.4 Linux 2.6 Microsoft Windows Server 2012 |
| Turkey | Linux 2.4 Microsoft Windows Server 2008 OpenBSD 4.0 |
| Indonesia | Linux 2.6 Linux 3.2 FreeBSD 6.2 |
| Argentina | Linux 4.4 Linux 2.6 Linux 3.2 |
| India | FreeBSD 6.2 Linux 2.4 Linux 2.6 |
| Italy | Linux 2.6 Linux 4.0 Linux 4.4 |
What are the top Common Vulnerabilities and Exposures (CVE) found in websites in national cyber perimeters?
A CVE or Common Vulnerability Exposure is an internationally recognised standard to define cybersecurity vulnerabilities found in software and tech stacks. CVEs are basically security flaws found in software which have different severities and if exploited can lead to, for example, data theft or service disruption. The Common Vulnerability Scoring System score or CVSS is also given for each top 3 vulnerability identified per country, the higher the CVSS score out of 10, the higher the severity and dangerousness of the CVE.
An explanation of each type of the top 3 CVEs identified for each country is given below as per the National (US) Vulnerability Database (NVD):
The top 3 CVEs identified per country alongside their severity is given below for the countries analysed:
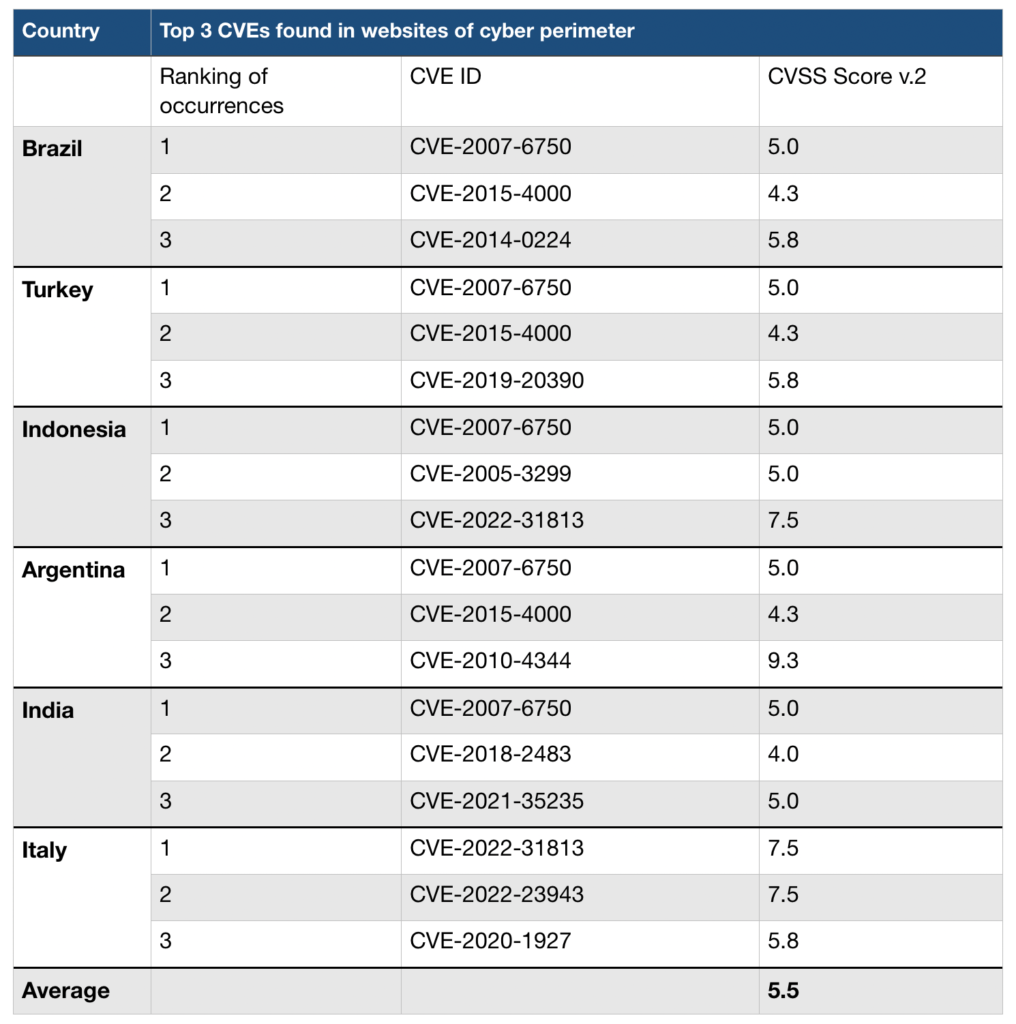
The CVEs mentioned in the above table are described below:
| CVE ID | CVSS score | Description |
| CVE-2007-6750 | 5.0 | AKA Slowloris, the Apache HTTP Server 1.x and 2.x allows remote attackers to cause a denial of service (daemon outage) via partial HTTP requests, as demonstrated by Slowloris, related to the lack of the mod_reqtimeout module in versions before 2.2.15. |
| CVE-2015-4000 | 4.3 | The TLS protocol 1.2 and earlier, when a DHE_EXPORT ciphersuite is enabled on a server but not on a client, does not properly convey a DHE_EXPORT choice, which allows man-in-the-middle attackers to conduct cipher-downgrade attacks by rewriting a ClientHello with DHE replaced by DHE_EXPORT and then rewriting a ServerHello with DHE_EXPORT replaced by DHE, aka the “Logjam” issue. |
| CVE-2014-0224 | 5.8 | OpenSSL before 0.9.8za, 1.0.0 before 1.0.0m, and 1.0.1 before 1.0.1h does not properly restrict processing of ChangeCipherSpec messages, which allows man-in-the-middle attackers to trigger use of a zero-length master key in certain OpenSSL-to-OpenSSL communications, and consequently hijack sessions or obtain sensitive information, via a crafted TLS handshake, aka the “CCS Injection” vulnerability. |
| CVE-2019-20390 | 5.8 | A Cross-Site Request Forgery (CSRF) vulnerability was discovered in allows a remote attacker to remove files on the server without a victim’s knowledge, by enticing an authenticated user to visit an attacker’s web page. The application fails to validate the CSRF token for a GET request. An attacker can craft a panel/uploads/read.json?cmd=rm URL (removing this token) and send it to the victim. |
| CVE-2005-3299 | 5.0 | PHP file inclusion vulnerability in grab_globals.lib.php in phpMyAdmin 2.6.4 and 2.6.4-pl1 allows remote attackers to include local files via the $__redirect parameter, possibly involving the subform array. |
| CVE-2022-31813 | 7.5 | Apache HTTP Server 2.4.53 and earlier may not send the X-Forwarded-* headers to the origin server based on client side Connection header hop-by-hop mechanism. This may be used to bypass IP based authentication on the origin server/application. |
| CVE-2018-2483 | 4.0 | HTTP Verb Tampering is possible in SAP BusinessObjects Business Intelligence Platform, versions 4.1 and 4.2, Central Management Console (CMC) by changing request method. |
| CVE-2021-35235 | 5.0 | The ASP.NET debug feature is enabled by default in Kiwi Syslog Server 9.7.2 and previous versions. ASP.NET allows remote debugging of web applications, if configured to do so. Debug mode causes ASP.NET to compile applications with extra information. The information enables a debugger to closely monitor and control the execution of an application. If an attacker could successfully start a remote debugging session, this is likely to disclose sensitive information about the web application and supporting infrastructure that may be valuable in targeting SWI with malicious intent. |
| CVE-2022-23943 | 7.5 | Out-of-bounds Write vulnerability in mod_sed of Apache HTTP Server allows an attacker to overwrite heap memory with possibly attacker provided data. This issue affects Apache HTTP Server 2.4 version 2.4.52 and prior versions. |
| CVE-2020-1927 | 5.8 | In Apache HTTP Server 2.4.0 to 2.4.41, redirects configured with mod_rewrite that were intended to be self-referential might be fooled by encoded newlines and redirect instead to an an unexpected URL within the request URL. |
| CVE-2010-4344 | 9.3 | Heap-based buffer overflow in the string_vformat function in string.c in Exim before 4.70 allows remote attackers to execute arbitrary code via an SMTP session that includes two MAIL commands in conjunction with a large message containing crafted headers, leading to improper rejection logging. |
The initial analysis of the cyber perimeter of Italy, India, Brazil, Indonesia, Argentina and Turkey has been completed using cloud technologies deployed within the European Union and for as much as possible, in Italy and open source softwares such as Nmap, OWASP ZAP and other cyber security and threat intelligence tools and the Python and Javascript programming languages. The identified key performance indicators or KPIs are just an initial list to define analytically and using hard evidence the resilience and strength of the cyber perimeters of the analysed countries. For each KPI a weight has been assigned to it – some have been assigned the weight of 0, hence not concurring in the calculation of a security score. Those KPIs with a positive or negative weight have been aggregated to calculate the cyber security score of a country, leading to a ranking or index of the cyber perimeters of countries taken into consideration.
